User and Group Provisioning via SSO & SCIM
Conveyor SCIM Integration
For users that have Conveyor integrated with a Single Sign On provider, we offer automated user provisioning via the SCIM protocol. This allows you to fully manage access to Conveyor via your identity provider, instead of having to invite users manually to Conveyor via the invite functionality.
Currently, our SCIM integration allows you to synchronize users that take the following actions:
- Push new users to your organizations as you add them to the identity provider integration
- Remove users if they are removed from the identity provider integration
- Remove users if they are de-activated within your identity provider
- Updates user email and name if they change it within your identity provider
- Manage specific access to Conveyor by mapping SCIM Groups to Conveyor Roles
To enable SCIM Provisioning you will need to select a default role to assign users to. Currently, we restrict newly provisioned users to only the lowest access user roles, which are currently the Trust Sharer and Assignee Only roles. Both of the roles allow read access to most objects within in Conveyor, with the Trust Sharer able to invite users to your Room.
Okta Walkthrough
This walkthrough assumes you already have an SSO integration with Conveyor active and working, and that your identity provider is Okta (though other SSO providers will work if they support SCIM 2.0). If you need help setting up Okta as a Single Sign On Provider, follow the instructions in our walkthrough here.
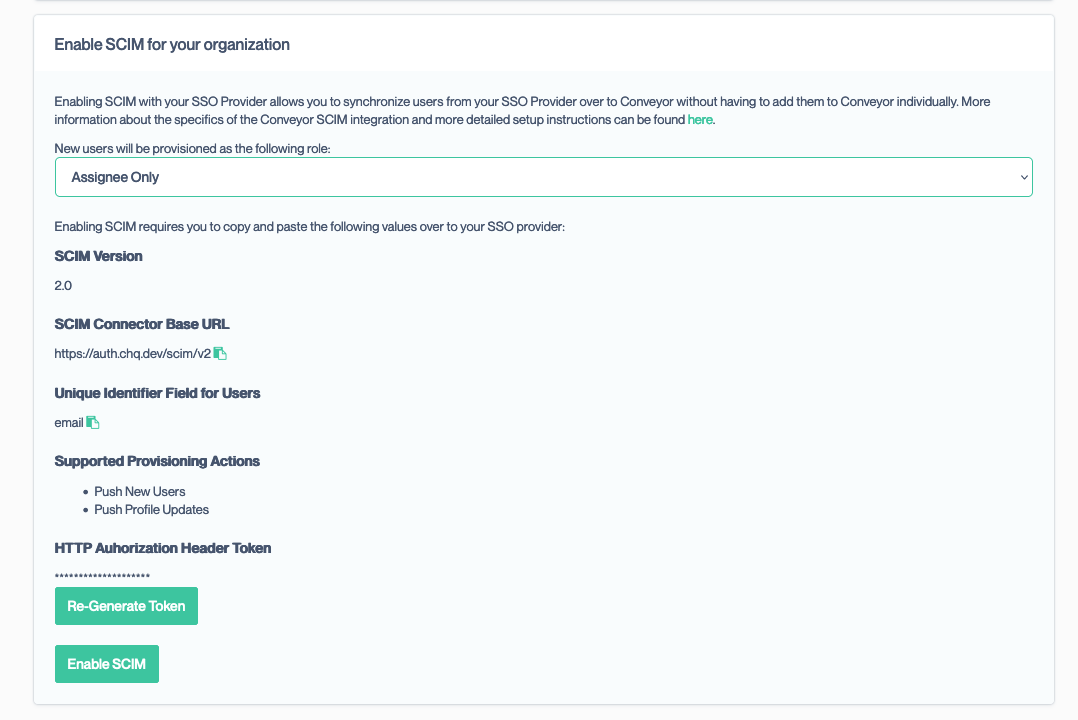
- Sign in to your Conveyor account and navigate to the Single Sign On settings and scroll to the Enable SCIM for your organization panel
- In a separate window or tab, sign in to Okta with an admin account
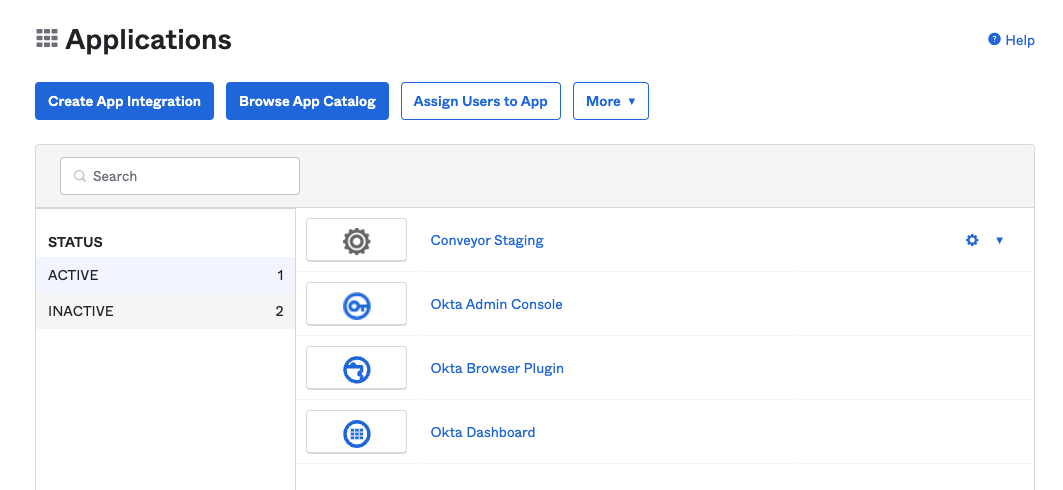
- Click Applications in the main menu
- Click on the application you have created for Conveyor (in this screenshot the app is named "Conveyor Staging")
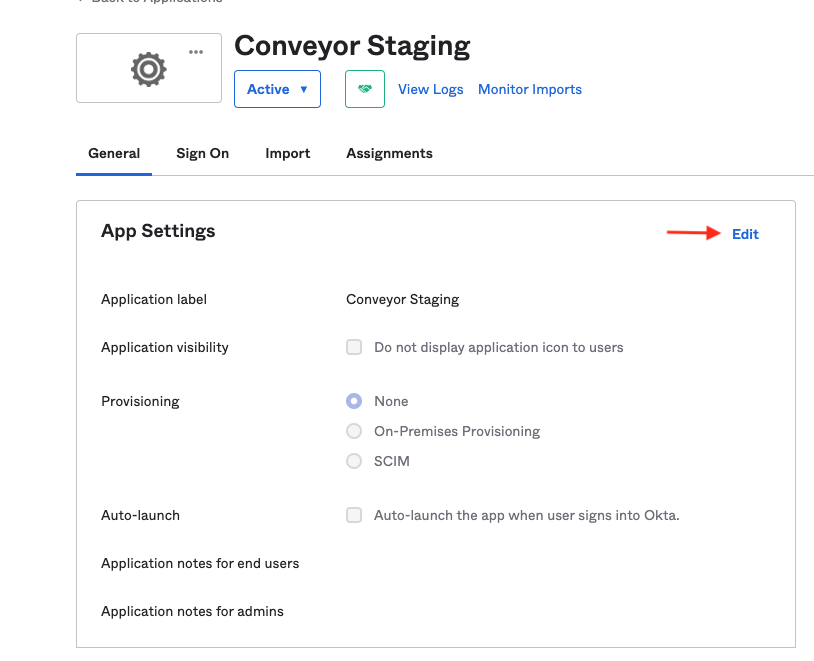
- Once in the application settings, click on the General tab then click on the Edit link in the upper right hand corner of the first panel.
- To right of the word "Provisioning", select the SCIM option and click Save in the lower right hand corner.
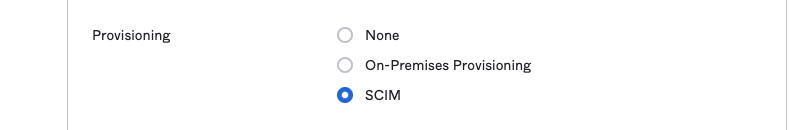
- After saving there should now be a Provisioning tab at the top of the application settings. Activate that tab and click the Edit link in the top right hand corner of the panel.
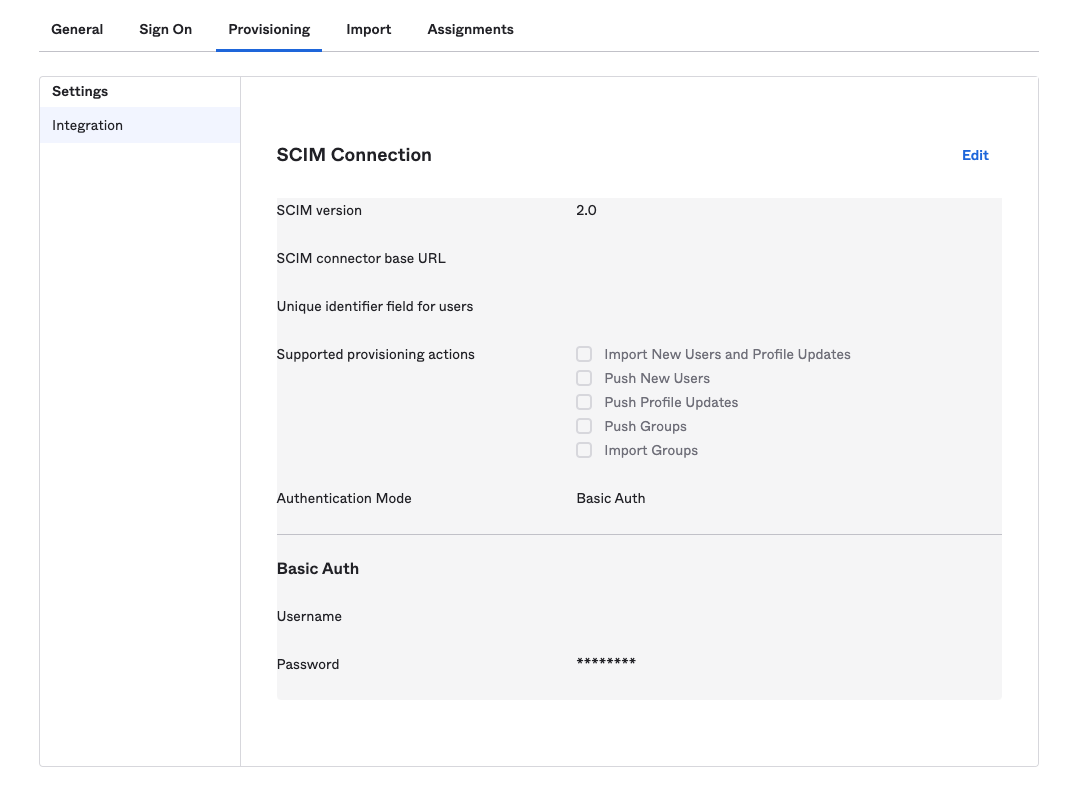
- We will now require values from your Conveyor account. Open the window containing the Conveyor Single Sign On settings.
- Select a default role to assign provisioned users to.
- Copy the SCIM Connector Base URL value and paste it into the corresponding input in the Okta SCIM Connection window
- Copy the Unique Identifier Field for Users value and paste it into the corresponding input in the Okta SCIM Connection window
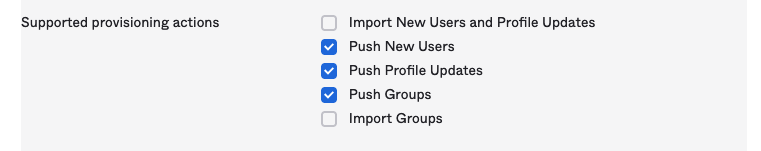
- In Okta, in the Supported Provisioning Actions section, enable the Push New Users and Push Profile Updates options. Optional: If you would like to synchronize SCIM Groups as well as Users, check the Push Groups options in addition to the two above options.
- In Okta, set the Authentication Mode option to HTTP Header
- In Conveyor, click on the Generate Token button. This should bring up a modal:
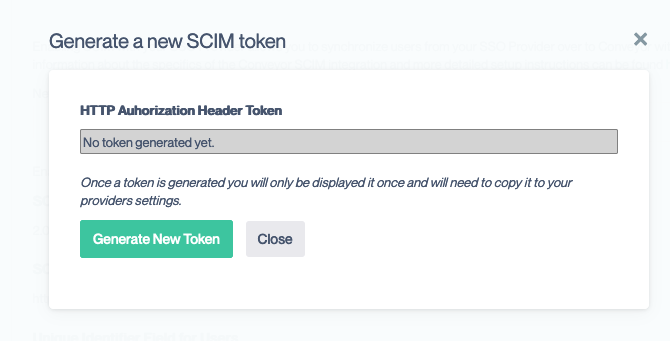
- Click Generate New Token and copy the token displayed. You will not be able to recover this token once you close the modal so it is important to copy it
- After you close the modal click Enable SCIM
- In Okta, paste the copied token into the Authorization input under the HTTP Header section. If you'd like to test that everything is connected properly, click the Test Connector Coniguration.
- After setting up all the options, your Okta screen should look like the following:
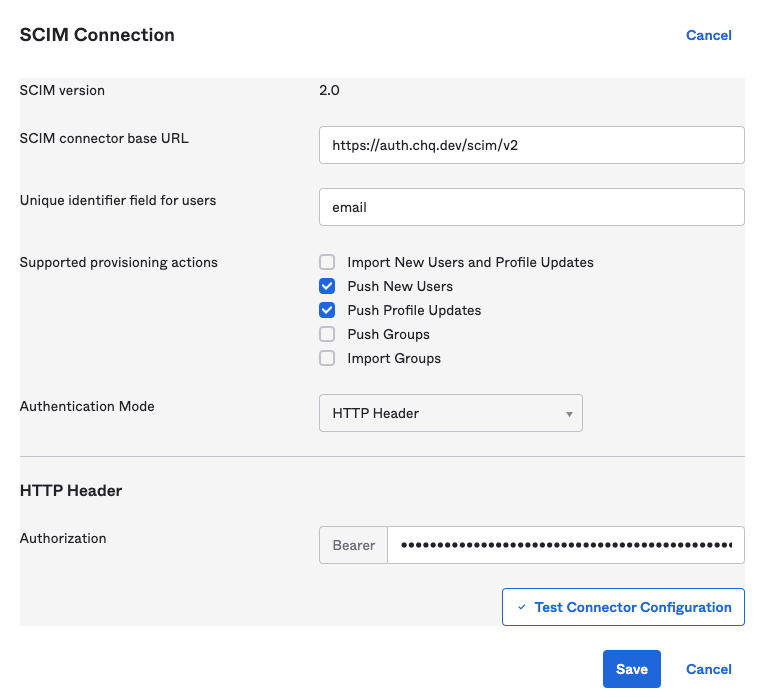
- Click Save at the bottom of the panel to save your options.
- Once the options have been saved, you see the following screen:
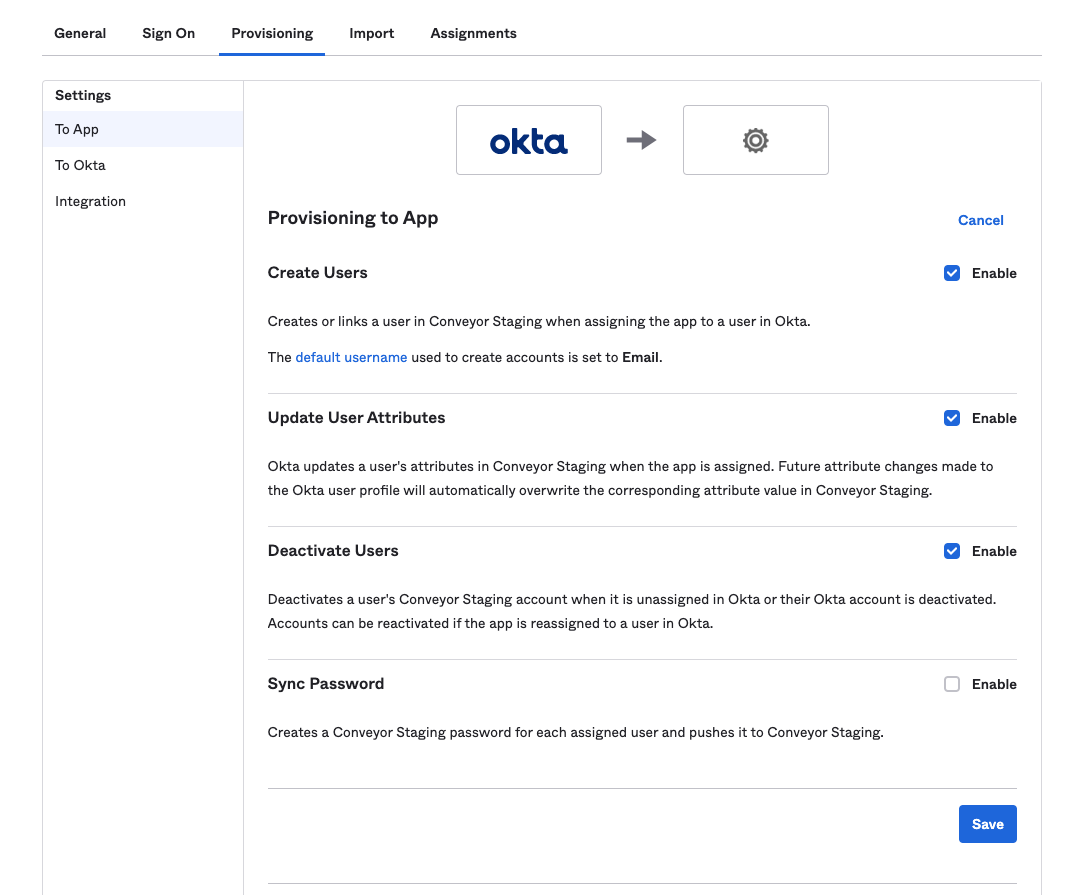
- Click Edit and select the Create Users, Update User Attributes and Deactivate Users options.
- When finished click Save
Congratulations! Your organization is now set up to start pushing users to Conveyor!
To test the integration, follow Okta's guide to assign users to an application and check your organization's Users page in Conveyor to verify that it worked.
SCIM Group Setup and Management
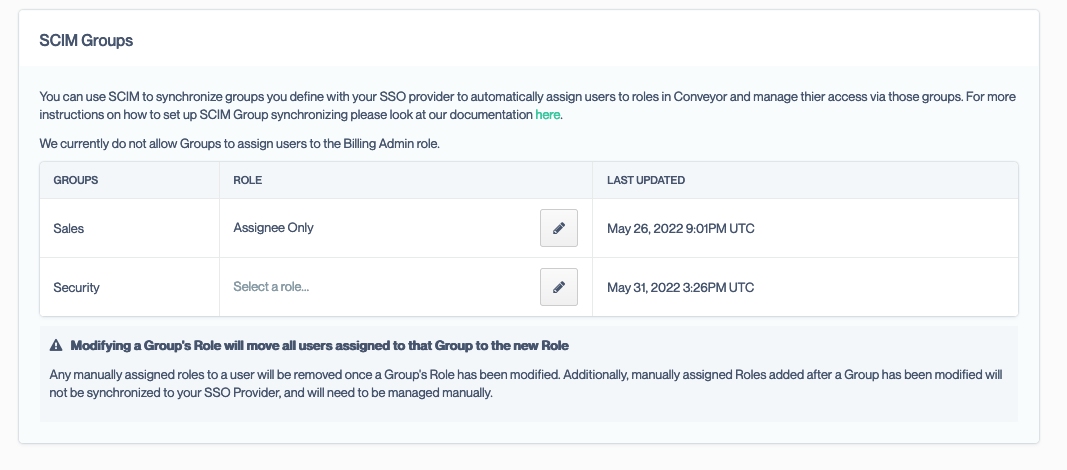
Conveyor also supports the ability to synchronize your Single Sign On Providers user groups with Conveyor Roles and manage your users assigned to Conveyor solely through SCIM Group Syncing.
To enable this functionality, in the screen mentioned in Step 16 of the above instructions, select the Push Groups option:
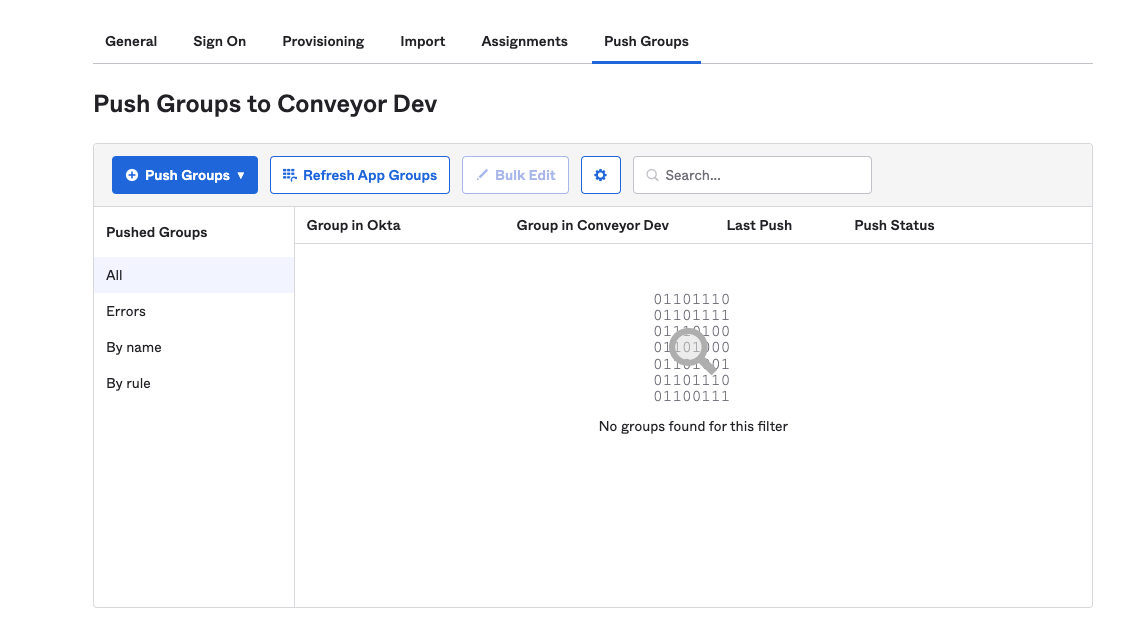
Then at the top of the SSO Application select the Push Groups tab:
Search for the groups you would like to synchronize to Conveyor (example here is searching by name):
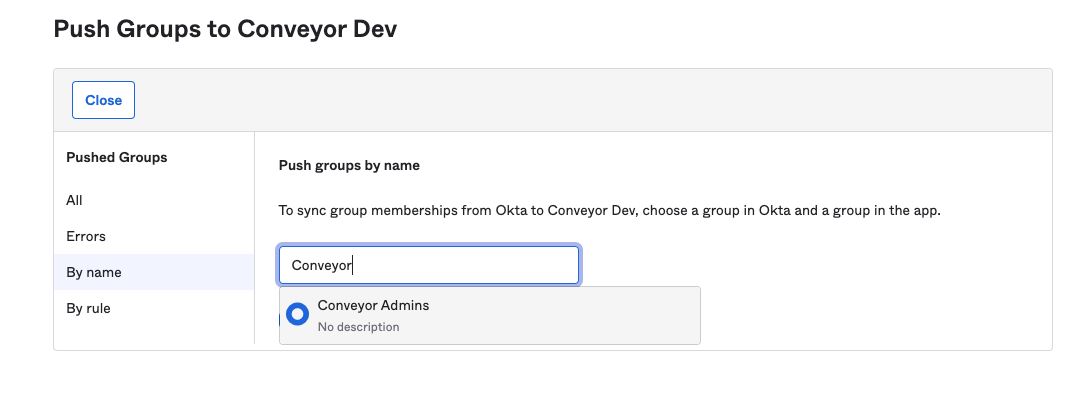
Select the group and click the Save button in the lower right-hand corner:
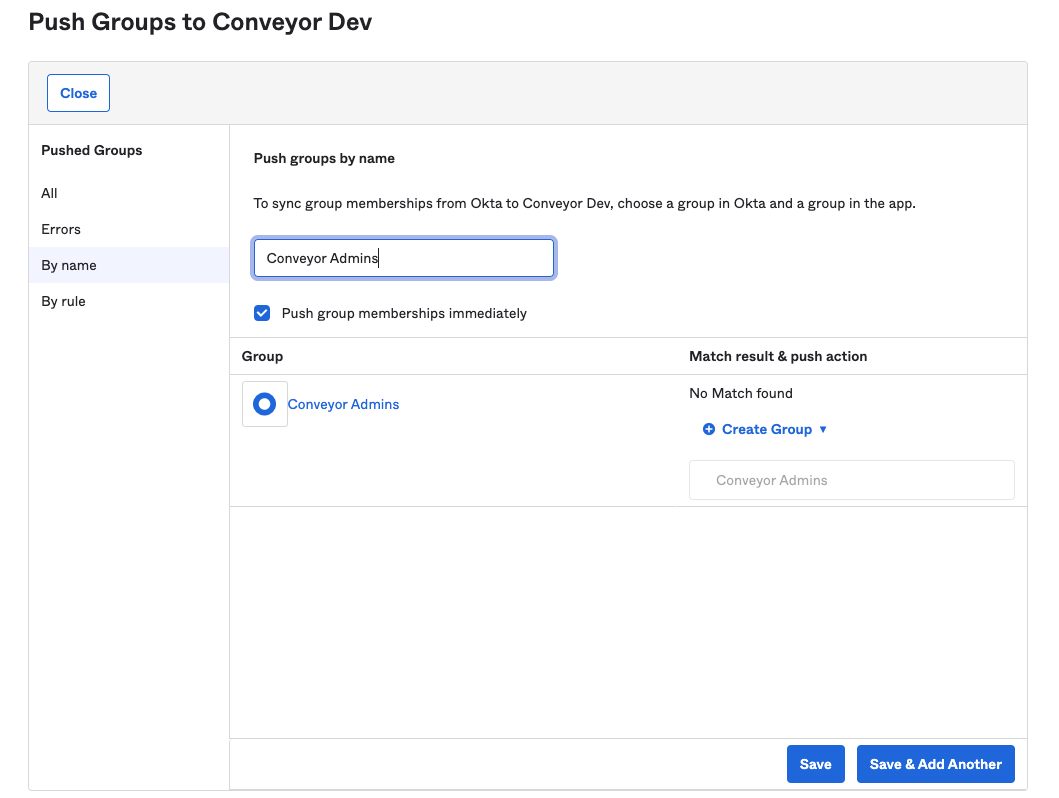
Finally, in the Assignments tab you can now select the same Group you selected to push and assign it to the Application:
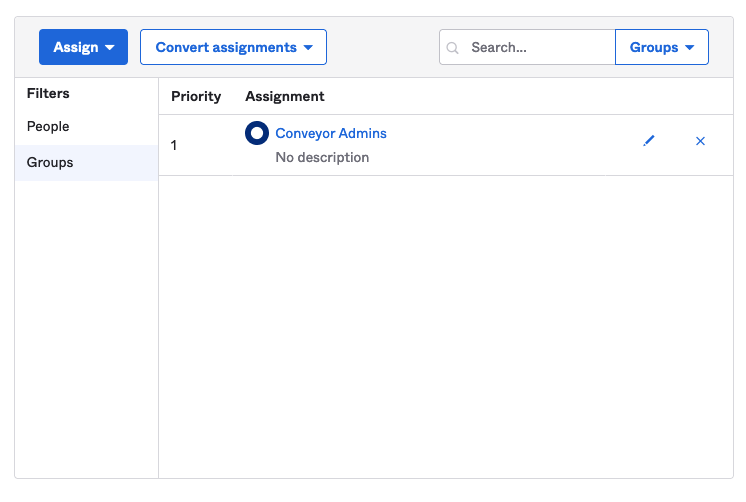
You should start to see groups you assign to the Conveyor application in your SSO Provider populate along with users in the section marked SCIM Groups. This panel allows you to map your SSO Providers Group(s) to Conveyor Roles, so that when a new user is added to the Group they will be automatically provisioned in Conveyor with the assigned Role.
When a new SCIM Group is provisioned in Conveyor, the Group is not provisioned with a Role by default. Users that were provisioned via the Group will be given the SCIM Default Role you designated in the above SCIM set up instructions.
You can modify the Role via the above-mentioned section and this will move all the assigned users over to the new Role designated by the Group.
NOTE: Once the new Role is assigned to a Group, the system removes the assigned User(s) from all other Roles that might have been assigned manually and assigns them only to Role designated by the Group. Additionally, once the user has been assigned the new Role, any manual Role assignment via the Conveyor Admin interface is not re-synchronized to your SSO provider, so if the user is removed from the Group, they will only be removed from the Group designated Role, which and not from any manually assigned Role.
In addition to the above, we currently do not allow the Billing Admin role to be automatically provisioned and managed via SCIM. If you need to assign a User to the Billing Admin role, this will need to be done via the Conveyor Admin interface. Additionally, as noted above, if a user is assigned to a SCIM Group in your SSO Provider but also is a Billing Admin and then removed, they will be removed from the Role designated by the SCIM Group, but will not be removed from the Billing Admin role.
Frequently Asked Questions
How can I provision news users into the Conveyor Admin role?
Currently, we only support provisioning users into the Assignee Only and Trust Sharer roles. Once the user has been provisioned and added to Conveyor, you can add them to additional roles via the Roles page in Conveyor
If I have added roles to a user and they are deactivated, does that remove them from all their roles?
Yes. However, we do not remove users from the Billing Admin role to prevent users from being locked out of their account.
Are the newly provisioned users able login to Conveyor without using SSO?
Yes, but if you enable the Require Single Sign On option they will not be able to access your organization unless using the Single Sign On URL.
What Okta attributes are synchronized to Conveyor?
We currently only synchronize the displayName and email attributes to Conveyor.
In Okta, there is a red checkmark next to a user on the assignments page. What does that mean?
If you notice a red-check mark on the assignments page like this:

This means that the user has failed to provision in Conveyor. Please click on the mark, copy the error message and let [email protected] know of the issue and we'll be happy to assist you.
After enabling SCIM, will all my current users assigned to the application be migrated to Conveyor?
No. Only users updated or added after SCIM is enabled are added.
Do you support importing users from Conveyor?
We do not at this time. If this would be helpful for your Organization, please let us know.
How can I learn more about SCIM?
There are many good references on the internet. Here are a few:
Updated 4 months ago
